Checking for Rogue Internet Connections with NetStat
I recently had an opportunity to try out Webroot Spy Sweeper and discovered 3 spyware programs on my computer that Grisoft's and Lavasoft's anti-spyware programs had previously failed to identify. It didn't look like these spyware programs were active i.e. I just had traces of them on my computer and it is possible that Spy Sweeper was reporting false positives, but I chose to act on the information and perform a thorough sweep.
I, like many people do, ran multiple anti-spyware programs because the general consensus is that no one spyware (or virus) detection program is 100% effective. Not only that, but there is no general consensus on which is the best detection program. Some online reviewers put McAfee's product up top, others recommend Lavasoft's, and ISP's just push their own solution. After hours of scanning, none of the programs found additional malware on my computer — a result I was pleased with.
I also used one additional piece of software — netstat — to check for unexpected Internet activity. This program ships with Microsoft Windows so it's essentially free. The netstat program “displays protocol statistics and current TCP/IP network connections.” You won't find an icon in your Start menu for this one. Instead you have to launch it using the Run option: The syntax I use is:
netstat -b 5
The -b parameter tells the program to list the executable that initiated the connection and the 5 parameter instructs netstat to re-display information every 5 seconds. And here's what the output will look like:
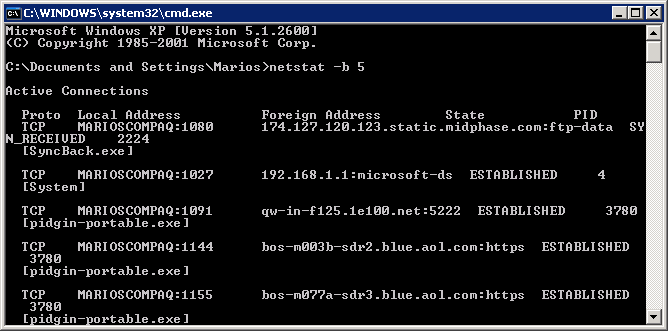
In the above sample, you can see the connections established by my computer when my web browser, firefox.exe, fetched a page from the CNN.com website.
If you run netstat with many programs open, the results will likely be unmanageable. So instead, I recommend you shutdown every program including e-mail readers, RSS feed readers, firewalls, and web browsers. After a minute or so, netstat should then show no active connections. If a connection is active, that's a sign you may have a rogue program communicating with the Internet.
Once you've got all connections closed or you've positively identified the remaining open connections, start up your web browser. Watch the list of connections that it establishes automatically. This will probably include various checks for browser and add-on upgrades along with a connection to the site you have set as your browser homepage. Inspect all of these connections and confirm they're going to websites you expect them to go to. Eventually, these connections will close at which point watch for new and unexpected ones being opened. If such connections do happen, this is another sign that your browser has been hijacked. Firewalls won't protect you from this sort of activity because you've undoubtedly marked your web browser as a trusted program.
Repeat this process of having a single application running and evaluate all of the connections made. This approach is effective because the days of viruses with a primary purpose of damaging computer files are largely gone. Instead, malware developers are more interested in setting up networks of zombie PCs, stealing your information, or logging your keystrokes — activities that all require Internet connections.



Leave a Reply